Custody
Safeguard your digital assets by switching to an insured and qualified digital asset custodian
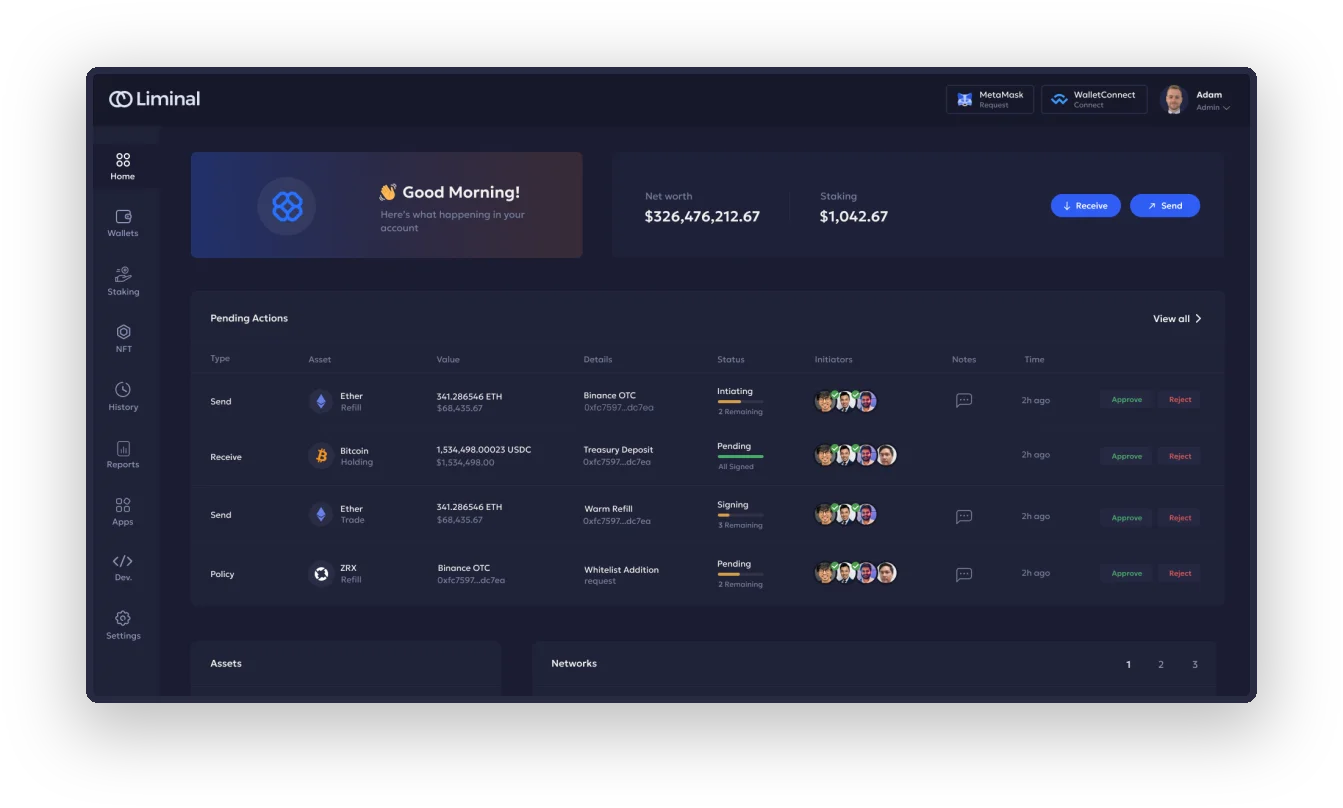
Explore the best-in-class custodial infrastructure embedded with enterprise-level compliance integrations
Discover the vital compliance checkpoints necessary for adherence. Benefit from seamless integration with industry-leading providers such as Notabene and TRM Labs for Travel Rule, KYT, AML, and CFT functionalities within Liminal’s custody solutions.
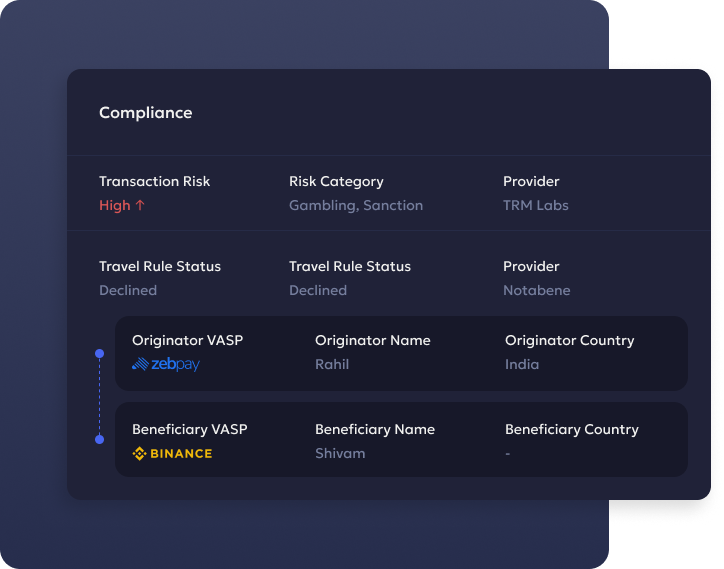
Liminal boosts Multi-Sig and MPC technology coupled with a Firewall setting to automate policy enforcement security in your wallet ecosystem
Insurance Protection
Cloud Node - Key Shard1
Remote location in Cloud Protection:
- Multi-layer access control
- 2FA Authentication
Mobile -
Key Shard2
- Secure Storage Mobile Phone
- Client Control
- Protection
- Secure Enclave
- Biometric
- Access Control
- 2FA Authentication
Recovery package - backup1
Insurance Protection
- Storage - Cloud
- Encrypted with Recovery Key generated by Enterprise Grade banking HSM
- Recovery Offline
- Valid only for Liminal Custody
Backup recovery key
- Storage - Custodian Controlled offline Encrypted media storage placed in access controlled bank lockers
- Protected with Recovery Key generated by FIPS 140-2 level 2/3 certified Offline HSM devices
- Offline recovery
Recovery package - backup2
- Storage - Escrow Storage
- Double Encryption:
- Encrypted with Recovery Key generated by Enterprise Grade banking HSM and Escrow Provider Key
- Recovery Offline
- Valid only for Liminal Custody
Liminal brings an expanded suite of features on top of custody
Highest Security Measures
Segregated Accounts
All Client accounts, and Liminal accounts and clients are further segregated from each other, ensuring that there is no commingling of assets financial separation and preventing any cross-contamination of funds.
Risk Mitigation
Get dedicated support from our custody operations team to run and manage your custody in your region
- Avail support for your custody operations in the business hour support window of 9 am - 6 pm on Monday-Friday
- All the queries are resolved by the regional entities of First Answers Pte Ltd as per the region's regulatory requirements
- Our dedicated team set up in each region will help run custody operations to help support various functionalities related to your custody wallets
Empowering institutions with tailor-made wallet operations in an efficient custody infrastructure
FAQs
Technology Risks:
Technology risks pertain to how the custodian handles private keys, covering storage, access, movement, processing, and deletion. These challenges are universal for custodians, but each addresses them differently, leading to varying levels of risk.
Business Risks:
For crypto custodians, business risks revolve around real-time transactions and decisions that sustain the enterprise. An exclusive concern is tokenomics, involving the utility of proprietary tokens, their issuance, management, and compliance.
Operational Risks:
Operational risks center on physical, personnel, and network security. The assessment also scrutinises customer interaction with the platform’s trading interface to identify potential exploitative transactions.
