Check out our latest blogs
Read through our updates covering feature launches, partnerships, thought leadership pieces and trending topics on how we are solving the security and custody problem for Web3 institutions

Team Liminal |
June 26, 2025
Digital asset custody has always been a balancing act between security and usability. While cold storage solutions provide the highest level of protection, they’ve traditionally required users to approve transactions without seeing what they’re signing. Recent attack vectors, including the ByBit Hack, have shown that attackers increasingly exploit human behaviour rather than smart contracts or blockchain infrastructure. Hence, Blind signing creates unnecessary risk, especially for institutional teams managing significant assets across multiple chains.
That’s why we’ve developed Blind Signing Protection for EVM Chains. This new capability brings full transaction visibility to EVM-compatible chains, allowing users to cross-verify the messages shown on their hardware drive before adding their signature to every transaction.
The Problem with Traditional Hardware Wallet Workflows
Most hardware wallets present users with cryptographic hashes when requesting transaction approval. These appear as long strings of random characters that provide no meaningful information about the transaction’s purpose or destination. Users must trust that the transaction they’re signing matches their intent, but they have no way to verify this.
This approach creates several challenges:
- Operational risk: Teams can’t validate transaction details, increasing the chance of errors
- Security vulnerabilities: Malicious actors can potentially trick users into signing unintended transactions
For organisations managing substantial digital assets, these blind spots represent unacceptable risk.
How Liminal’s Solution Works
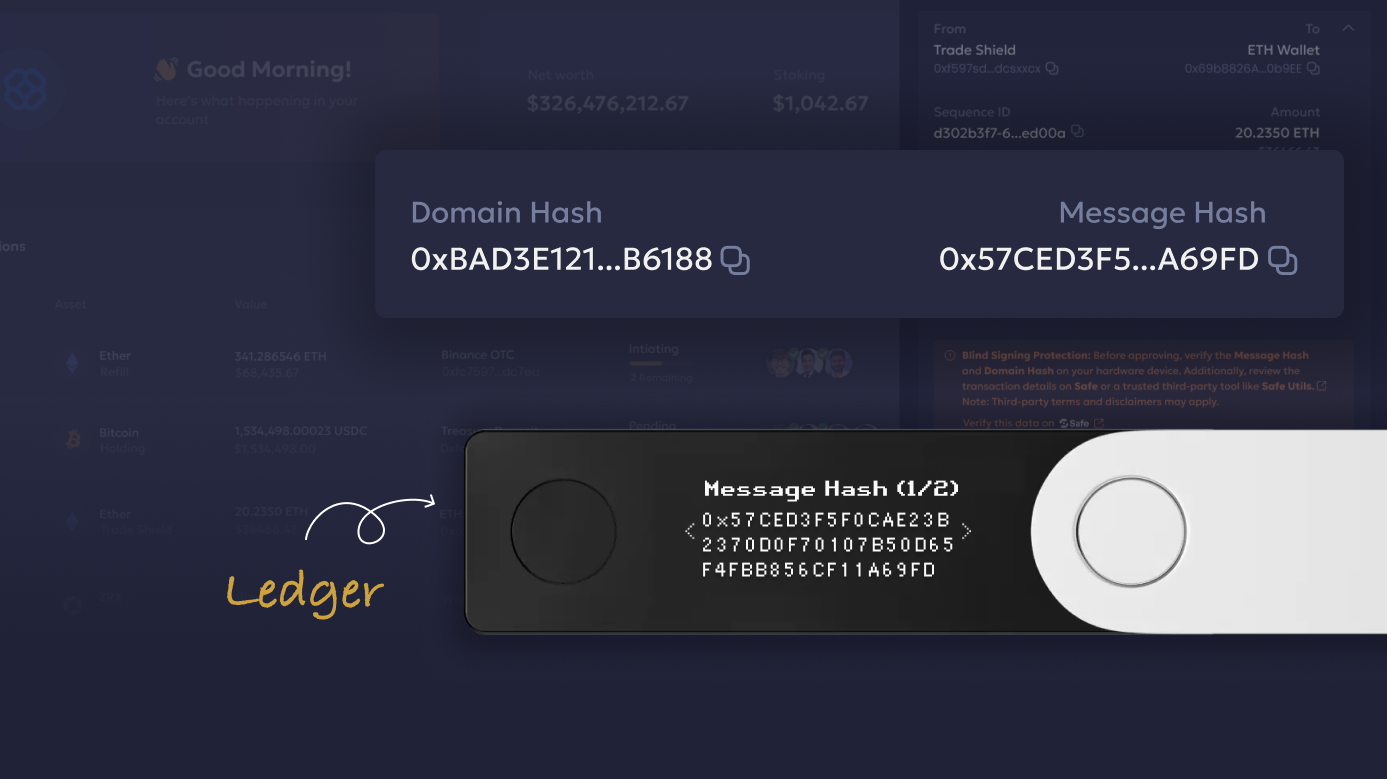
Blind Signing Protection for EVM chains transforms the approval process by displaying human-readable transaction data directly in the Liminal dashboard. In Ethereum’s EIP-712 (Typed Signatures), the message hash and domain hash are used to create a unique and verifiable signature for a message
When a signing request is generated, users can now see:
- Message Hash: A cryptographic hash of the message’s data. This data includes things like the recipient address, value, and the input data associated with the transaction.
- Domain Hash: A cryptographic hash of the domain object, which contains information about the chain ID and the address of your Safe wallet.
These values can be independently verified using external tools and manual decoding methods, giving signers complete confidence in what they’re approving.
The feature works seamlessly with Ledger wallets, without requiring changes to your current setup or workflow.
Why This Matters for Institutional Users
Transaction transparency isn’t just about convenience – it’s about maintaining the high security standards that institutional custody demands.
- Improved Operational Security: Teams can catch errors before they occur. Whether it’s a wrong address, incorrect amount, or unexpected contract interaction, signers can spot issues during the approval process rather than after funds have moved.
- Multi-Stakeholder Confidence: When multiple parties need to approve transactions, everyone can independently verify the transaction details. This builds trust and reduces the back-and-forth typically required for complex approvals.
- Getting Started: Blind Signing Protection is available immediately for all EVM chains on Liminal’s Cold Multisig Wallets. The feature integrates directly with your existing Ledger devices and requires no implementation.
Looking Forward
This release represents our commitment to eliminating unnecessary risks in digital asset custody. By providing transparency at the moment of signing, we’re helping institutions maintain the security benefits of cold storage while gaining the operational clarity they need.
We’re already working on expanding support to additional blockchain networks and exploring ways to provide even richer transaction context in future releases.
Your feedback helps shape our development priorities. If you have questions about implementation or suggestions for future enhancements, our team is always available to discuss how we can better serve your custody needs.
Liminal provides institutional-grade digital asset custody infrastructure designed for security-conscious organisations. Contact our team at [email protected] to learn more about how Blind Signing Protection can strengthen your operational security.