Liminal HSM Vault provides complete offline protection and policy-based control for digital assets. Built with Securosys HSM, it ensures private keys never go online while maintaining full regulatory compliance.

Traditional custody systems were not built for the complexity, compliance, and control institutions need today. Institutions managing digital assets face critical risks:
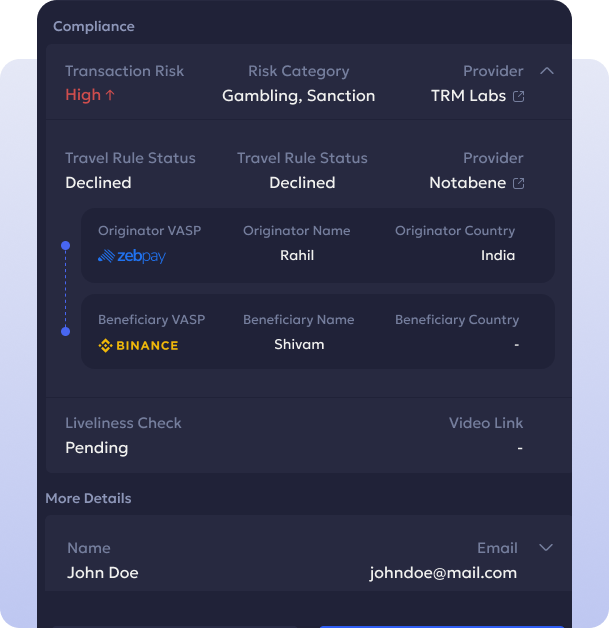
HSM Vault enables institutional grade cold storage through a hybrid HSM and MPC architecture.
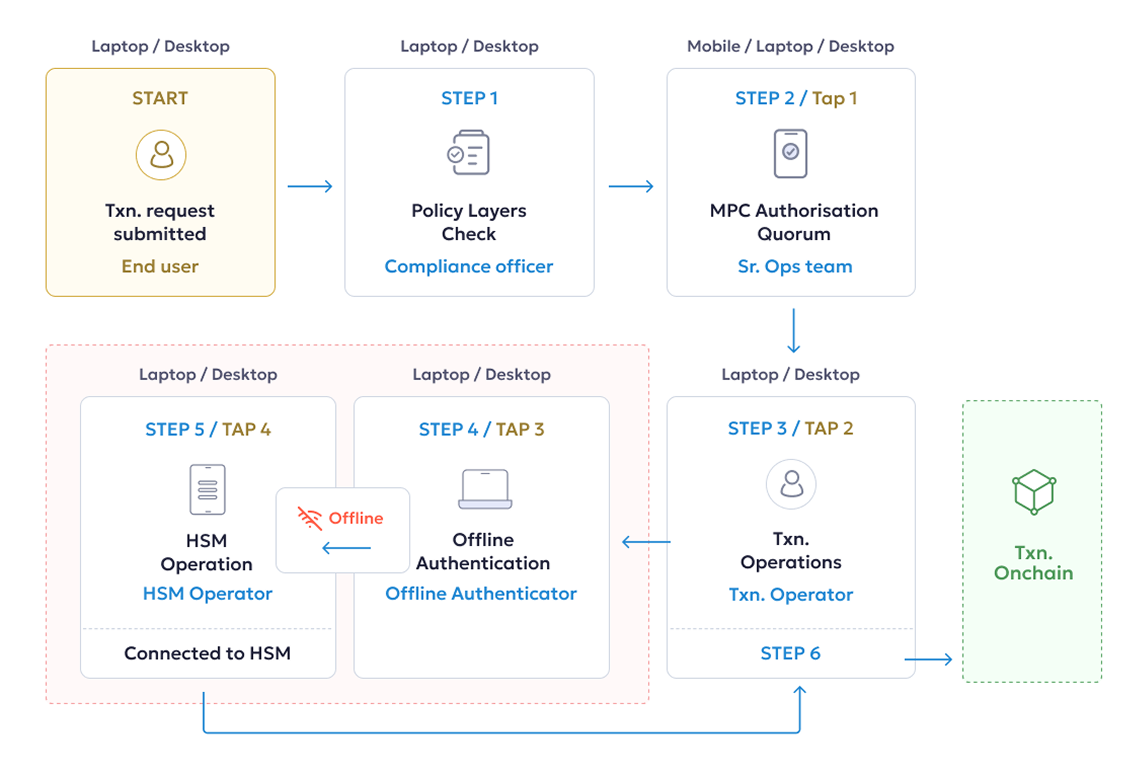
Throughout the process, private keys remain inaccessible, ensuring absolute cold security.
